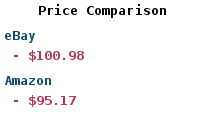Risk Centric Threat Modeling
Process for Attack Simulation and Threat Analysis

Book Description
This book introduces the Process for Attack Simulation & Threat Analysis (PASTA) threat modeling methodology. It provides an introduction to various types of application threat modeling and introduces a risk-centric methodology aimed at applying security countermeasures that are commensurate to the possible impact that could be sustained from defined threat models, vulnerabilities, weaknesses, and attack patterns.Risk Centric Threat Modeling: Process for Attack Simulation and Threat Analysis is a resource for software developers, architects, technical risk managers, and seasoned security professionals.
Book Details | |
| Publisher: | Wiley |
| By: | Tony UcedaVelez, Marco M. Morana |
| ISBN-13: | 9780470500965 |
| ISBN-10: | 0470500964 |
| Year: | 2015 |
| Pages: | 696 |
| Language: | English |
Book Preview | |
| Online | Risk Centric Threat Modeling |
Paper Book | |
| Buy: | Risk Centric Threat Modeling |